Topics covered
Java RMI exploitation
Adduser privilege escalation
Enumeration
Tomcat
The web server is hosting Tomcat; however, no exploitable vectors were identified.
Java RMI
Java Remote Method Invocation (RMI) is an object-oriented Remote Procedure Call (RPC) framework that enables an object in one Java Virtual Machine (JVM) to invoke methods on an object residing in another JVM.
The Beanshooter tool was used for vulnerability scanning and exploitation, revealing that authentication is not enabled and some credentials for the Tomcat users are exposed.
Exploitation
According to the repository for Beanshooter tool , the recommended method for achieving remote code execution (RCE) is as follows:
Command execution via the
standardaction is blind and you do not receive the output of your command. Moreover, by default your command is passed toRuntime.exec(String str), which does not support special shell features. If you want to use shell features, use the--exec-arrayoption and specify your command like this:'sh -c echo "my cool command" > /tmp/test.txt'. With--exec-array, beanshooter splits the specified command in three parts and passes them toRuntime.exec(String[] arr). However, it is generally recommended to use the TonkaBean deployment for executing commands:
beanshooter standard 172.17.0.2 9010 tonka
beanshooter tonka shell 172.17.0.2 9010The huge advantage compared to the regular
tonka deployaction is that deployment via the StandardMBean does not require an outbound network connection.
The exact steps outlined in the repository were followed, successfully resulting in a shell.
For a more stable shell, nc (Netcat) can be utilized. This can be achieved by upgrading the initial shell to a Netcat reverse shell, allowing for better control and reliability.
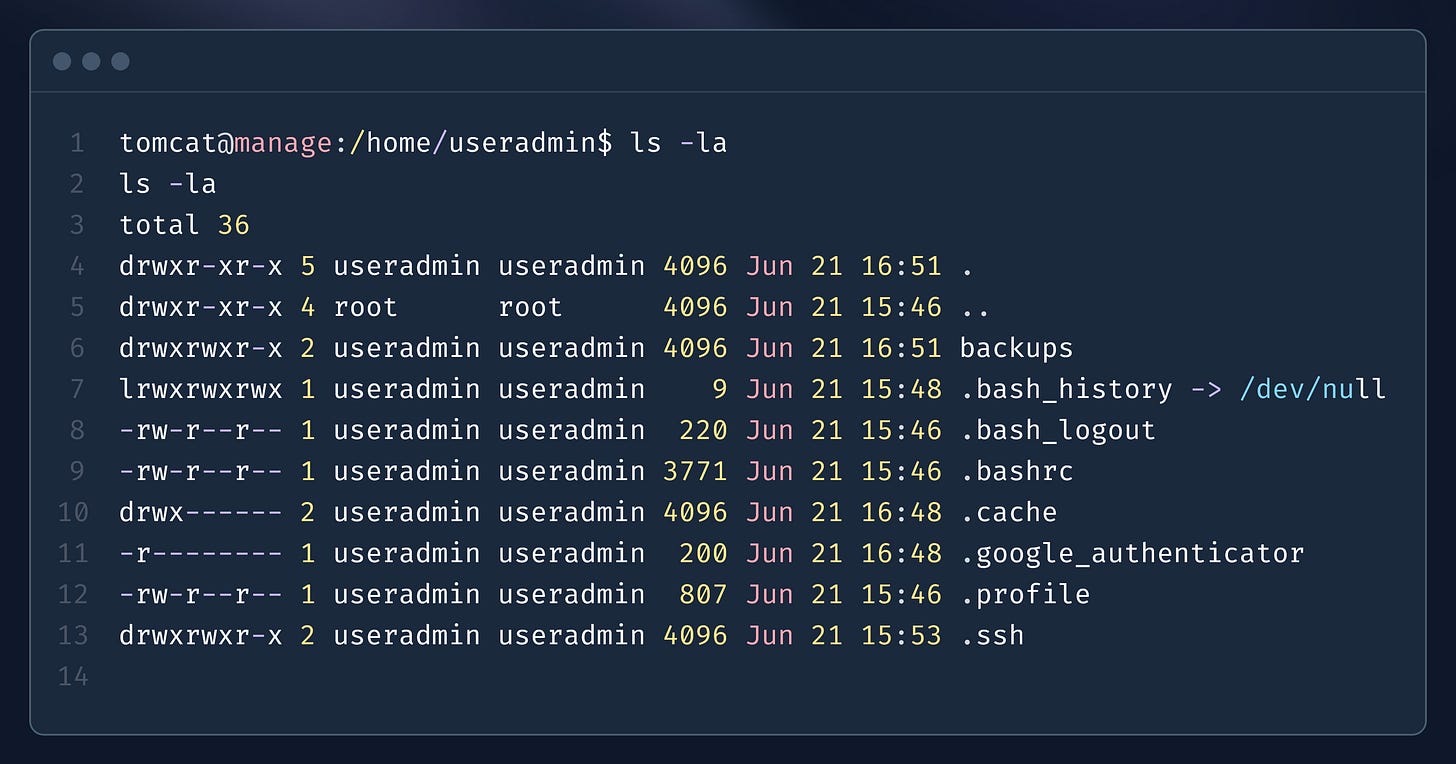
In the user directory, where only read access was available, a backups folder and a .google_authenticator file were discovered.
To transfer backup file netcat was used. Netcat can work in both receiving and sending modes, making it versatile for simple file transfers between two systems.
The presence of .google_authenticator revealed information related to multi-factor authentication (MFA),
An SSH private key was also discovered, which, when used in conjunction with the multi-factor authentication (MFA) code, facilitated access to the system.
Privilege escalation
Adduser can be used to create a new admin user and group during system initialization if no admin user or group is present. By default, Ubuntu includes an admin group in the /etc/sudoers file, which grants this group and user sudo privileges. When specifying "admin" in the configuration, the system will automatically establish an admin user and group with elevated permissions.
References
https://github.com/qtc-de/remote-method-guesser
https://github.com/qtc-de/beanshooter
https://askubuntu.com/questions/43317/what-is-the-difference-between-the-sudo-and-admin-group
https://swisskyrepo.github.io/PayloadsAllTheThings/Java%20RMI/#detection